A Dapp built on Solana and powered by Web3Auth , to manage your SOL via smart vaults and protect yourself from market FOMO.
FOMO buys and panic sells implies zero discipline.
But what if you could enforce your best intentions on-chain?
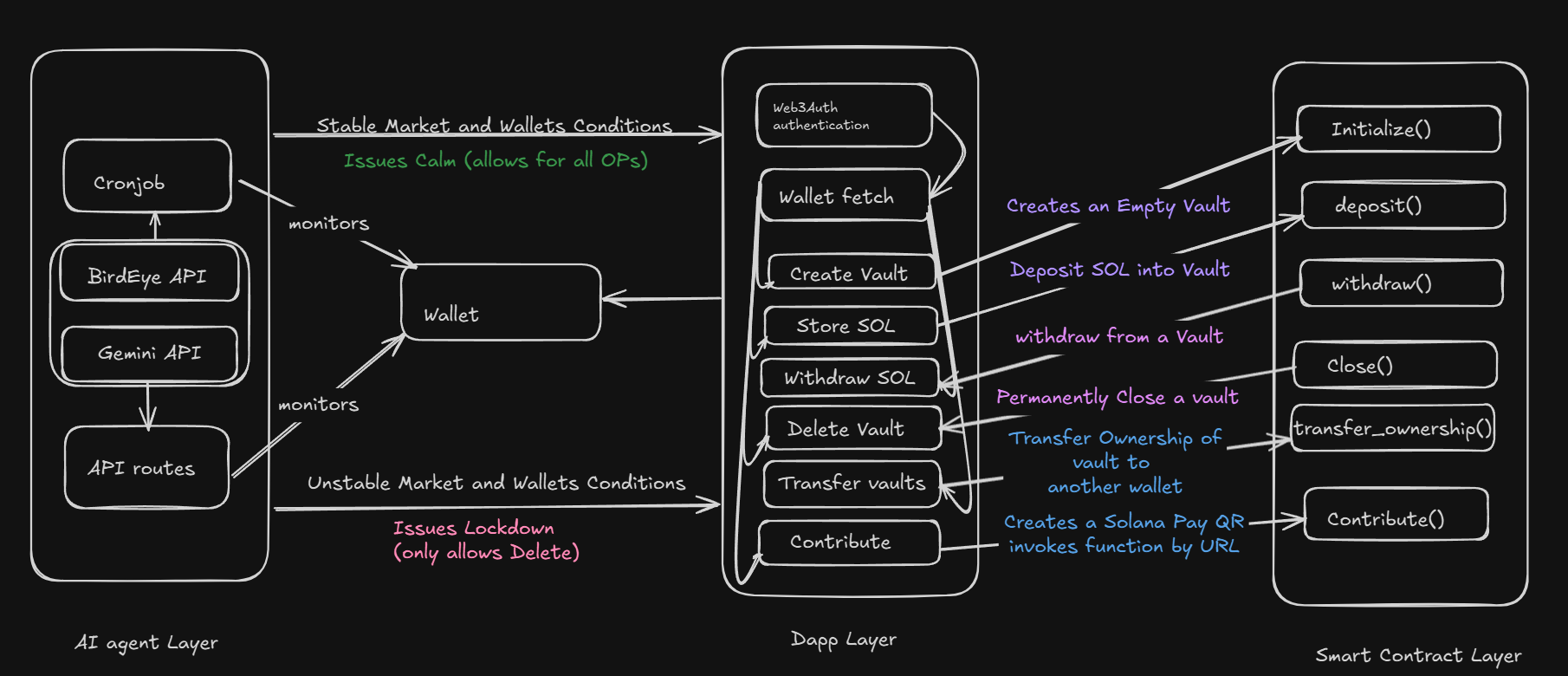
Auri is a Dapp on Solana that automates financial discipline by letting users keep their SOL in AI agent monitored vaults. The agent monitors market risk and locks your funds to prevent FOMO, ensuring you dont take a decision you would regret later.
Deployed Link : https://auri-gules.vercel.app/
GitHub: https://github.com/ranzorldy/Auri
Because emotional decisions are the most expensive mistakes in crypto and Web3 space.
Auri provides the on-chain discipline that standard wallets lack, creating a crucial buffer between market chaos and your assets to preserve your long-term wealth.
Auri is an smart vault Dapp on Solana designed to protect your assets and automate financial discipline. It combines secure, on-chain storage with AI monitor agents to shield you from market volatility and emotional decisions.
🌐 Seamless Sign-On: Get started in seconds. Auri integrates with Web3Auth, allowing you to sign up and sign in using your favorite social accounts.
🤖 AI-Guarded Vaults: Create smart vaults to secure your SOL. Our AI agent monitors market risks 24/7, automatically locking your vault to prevent impulsive FOMO buys.
📲 Effortless Contributions: Easily accept contributions from anyone, anywhere. Each vault comes with a unique Solana Pay QR code, perfect for community goals or family savings.
🤝 Transferable Ownership: Pass on your digital assets securely. Auri allows you to transfer the complete ownership of a vault to a trusted friend or family member.
🎯 Set & Track Goals: Attach a purpose to your savings. Set personal financial goals for each vault and track your progress directly from the dashboard.
🧠 Intelligent Analysis: Stay informed with AI-powered insights. Get a clear, logical explanation of token risks and understand why your vault's security state changes.
🌱 Earn While You Secure (Coming Soon): Put your assets to work. Stake your SOL directly from the vault to earn staking rewards, growing your holdings while they stay protected.
Step 1: User onboards to our app and signs in using web3Auth
Step 2: User goes on to create vaults and put SOL in them
Step 3: User may choose to add more, take out or transfer it to friend or alt or open for Contribution from others
Step 4: AI agents automatically monitors users on chain activity and wallet tokens and present market conditions .
Step 5: If any suspicious activity follows like market crashes or user buys SPL tokens with low liquidity and other unfavourable things, AI agent lockdowns all the vaults , hence preventing user from doing anything risky with his saved funds.
SSR reads cookies → cookieToWeb3AuthState → pass to Web3AuthProvider for consistent hydration.
Web3AuthProvider configures modal (Sapphire Devnet, SSR) and wraps the app.
SolanaAuthProvider consumes Web3Auth hooks, manages Connection, persists userInfo/address, and exposes a simple wallet context for the app.
UI and features use hooks (useWeb3Auth, useWeb3AuthConnect, useSolanaWallet, useSignAndSendTransaction) to connect, show wallet UI, get accounts, and sign transactions. A fallback SolanaWallet adapter is dynamically imported if needed.
Key files: providers/Web3AuthProvider.tsx, app/layout.tsx, providers/SolanaAuthProvider.tsx.
Key hooks: useWeb3Auth, useWeb3AuthConnect, useWeb3AuthDisconnect, useWeb3AuthUser, useSwitchChain, useSolanaWallet, useSignAndSendTransaction.
npm install
npm run dev
# open http://localhost:3000Landing is at /.
Dashboard lives under /dashboard.
Use the sidebar’s Connect action (Web3Auth) to authenticate a wallet session.
Build and start:
npm run build
npm startCreate .env.local in the repo root. Fill as needed (optional keys are marked).
# Solana RPCsNEXT_PUBLIC_SOLANA_RPC_URL=https://api.devnet.solana.com # optional; client-side in SolanaAuthProviderSOLANA_RPC_ENDPOINT=https://api.devnet.solana.com # used by /api/pay/contributeSOLANA_RPC_MAINNET=https://api.mainnet-beta.solana.com # used by /api/risk/analyze when chain fetch is enabled# BirdEye (strongly recommended to avoid 429)BIRDEYE_API_KEY=your_birdeye_key# Risk engine model key (optional: enables Gemini analysis path)GEMINI_API_KEY=your_gemini_key # or GOOGLE_GEMINI_API_KEY# Risk engine behaviorRISK_CHAIN_FETCH=0 # set to 1 to fetch wallet SPL holdings on-chain# Market API overrideMSOL_MINT=mSoLzYCxHdYgdzU16g5QSh3i5K3z3KZK7ytfqcJm7So# Web3Auth (client id currently in code; you can move it to env if desired)NEXT_PUBLIC_WEB3AUTH_CLIENT_ID=your_web3auth_client_idNotes:
/api/risk/analyze uses only BirdEye market data by default. Set GEMINI_API_KEY to enable Gemini JSON reasoning.
/api/risk/analyzeAnalyzes one or more SPL token mints for risk signals. Uses BirdEye market data and a simple local ruleset; optionally invokes Gemini for JSON reasoning.
Body:
{"walletAddress": "optional_solana_pubkey","mints": ["optional_mint1", "optional_mint2"]}Behavior:
If RISK_CHAIN_FETCH=1 and walletAddress is set, it will fetch detected SPL token mints from chain (mainnet RPC) and analyze up to 25 tokens.
If no tokens are found, analyses SOL as a fallback (So1111...).
Example:
curl -X POST http://localhost:3000/api/risk/analyze \
-H "Content-Type: application/json" \
-d '{
"walletAddress": "YOUR_WALLET_ADDRESS",
"mints": []
}'Response (abridged):
{"walletAddress": "...","results": [
{
"mint": "...",
"metrics": { "liquidityUsd": 12345, "priceChange1hPercent": 12.3, ... },
"rules": [ { "id": "liquidity", "ok": true, ... } ],
"gemini": { "risk": "LOW_RISK", "justification": "...", ... },
"birdseye": { "price": 0.01, "liquidity": 12345, ... }
}],"lock": false,"state": "Calm","debug": { "total": 1, "model": "gemini-2.5-flash" }}Env used: BIRDEYE_API_KEY, GEMINI_API_KEY or GOOGLE_GEMINI_API_KEY (optional), SOLANA_RPC_MAINNET, RISK_CHAIN_FETCH
/api/pay/contributeImplements a Solana transaction builder compatible with wallet flows for to be encoded by Solana Pay (GET handshake + POST transaction). Defaults to Devnet.
GET handshake (label/icon):
curl "http://localhost:3000/api/pay/contribute?name=MyVault&vault=VaultPubkey&amount=0.1"POST build transaction:
curl -X POST "http://localhost:3000/api/pay/contribute?name=MyVault&vault=VaultPubkey&amount=0.1" \
-H "Content-Type: application/json" \
-d '{"account":"ContributorPubkey"}'Response (abridged):
{"transaction": "base64_serialized_tx","message": "Contribute 0.1 SOL to MyVault"}Under the hood:
Encodes an instruction for PROGRAM_ID from lib/constants.ts using Anchor discriminator global:contribute and arguments (name: string, amount: u64).
Sets feePayer = contributor and fills recent blockhash.
Env used: SOLANA_RPC_ENDPOINT
AuraVault AccountThis is the main data structure that stores all the information for a single vault.
Field | Type | Description |
|---|---|---|
|
| The immutable public key of the user who first created the vault. Used for deriving the vault's unique address (PDA). |
|
| The public key of the current owner of the vault. This is the only key authorized to perform owner-restricted actions. This field is mutable via |
|
| A unique name for the vault, up to 64 bytes. Used as a seed for the PDA. |
|
| The bump seed for the vault's PDA. |
Account Size: 139 bytes (8 for discriminator + 32 for creator + 32 for owner + 4 + 64 for name + 1 for bump)
initializeInitializes a new, empty vault with a unique name. The user who calls this function becomes both the creator and the initial owner.
Arguments:
name: String - The desired name for the new vault (max 64 bytes).
Accounts (Context<Initialize>):
vault: The vault account to be created (PDA). Must be init.
user: The signer who is creating and paying for the vault.
system_program: Required by Solana for account creation.
depositDeposits SOL from the owner's wallet into the vault. This is an owner-restricted action.
Arguments:
_name: String - The name of the vault (required for PDA derivation).
amount: u64 - The amount of SOL (in lamports) to deposit.
Accounts (Context<Deposit>):
vault: The vault account to deposit into.
owner: The current owner of the vault. Must be a signer.
system_program: Required for the transfer instruction.
Security: Fails if the signer is not the current owner.
withdrawWithdraws SOL from the vault to the owner's wallet. This is an owner-restricted action.
Arguments:
_name: String - The name of the vault (required for PDA derivation).
amount: u64 - The amount of SOL (in lamports) to withdraw.
Accounts (Context<Withdraw>):
vault: The vault account to withdraw from.
owner: The current owner of the vault. Must be a signer.
system_program: Required for the transfer instruction.
Security: Fails if the signer is not the current owner.
transfer_ownershipPasses ownership of the vault to a new Solana wallet. This is an owner-restricted action and is irreversible by the original owner.
Arguments:
_name: String - The name of the vault (required for PDA derivation).
new_owner: Pubkey - The public key of the wallet that will become the new owner.
Accounts (Context<TransferOwnership>):
vault: The vault account whose ownership is being transferred.
owner: The current owner of the vault. Must be a signer.
Security: Fails if the signer is not the current owner.
contributeAllows any wallet to deposit SOL into a vault. This is a public function designed for contributions or funding via Solana Pay.
Arguments:
_name: String - The name of the vault (required for PDA derivation).
amount: u64 - The amount of SOL (in lamports) to contribute.
Accounts (Context<Contribute>):
vault: The vault account to contribute to.
contributor: The wallet sending the contribution. Must be a signer.
system_program: Required for the transfer instruction.
Security: This function is public and can be called by anyone.
closeCloses the vault account and returns all remaining SOL (including rent) to the current owner. This is an owner-restricted action.
Arguments:
_name: String - The name of the vault (required for PDA derivation).
Accounts (Context<CloseVault>):
vault: The vault account to be closed.
owner: The current owner of the vault. Must be a signer and will receive the SOL.
Security: Fails if the signer is not the current owner.
Error Name | Code | Description |
|---|---|---|
|
| The transaction was signed by a wallet that is not the current |
|
| The vault does not have enough SOL to complete the requested withdrawal. Triggered by |
|
| The provided name for a new vault exceeds the maximum length of 64 bytes. Triggered by |
Our current version of Auri. provides a robust foundation for secure, intelligent asset management. The following features represent our vision for expanding the platform's utility, deepening its security, and creating a more engaging user experience.
The most immediate next step is to make the SOL held within our vaults productive. We plan to integrate directly with leading liquid staking protocols like Marinade and Jito. This will allow users to stake their SOL directly from the Auri. interface, earning staking yield on their assets while they remain protected by our AI agent. This transforms the vault from a simple security tool into a powerful, wealth-building instrument.
We will expand Auri. to become a true portfolio management tool by adding support for all SPL tokens and NFTs. Users will be able to create specialized vaults for their stablecoins, long-term holds, and even their valuable digital collectibles. The AI agents's analysis engine will be upgraded to provide risk assessments for any SPL token, offering comprehensive protection across a user's entire on-chain portfolio.
To offer unparalleled security, we will introduce and enhance the AI agent and allowance system. Users will be able to:
Set a fixed daily withdrawal limit to prevent wallet drain attacks and enforce disciplined spending.
Appoint a Agent who can trigger a temporary Caution state.
Appoint an Emergency Agent who is the only party that can access funds during a full Lockdown. This creates a multi-layered, on-chain security protocol that is fully customizable by the user.
To boost user engagement and retention, we will introduce gamification elements. Features like "HODL Streaks" will reward users for not making withdrawals, and achievements will be awarded for reaching savings goals. We also plan to introduce multi-owner vaults, allowing groups of friends or DAOs to collectively manage a shared pool of funds with customizable signing rules, perfect for collaborative projects and investments.
BirdEye 429 / empty data:
Set BIRDEYE_API_KEY and retry; the APIs implement basic caching and throttling.
Wallet not connecting:
Confirm Web3Auth client id configuration and allow pop-ups.
Ensure you’re on Devnet unless you changed RPCs.
Risk analysis returns limited fields:
Only available fields are used. Set RISK_CHAIN_FETCH=1 and SOLANA_RPC_MAINNET to enrich input from on-chain.